[OSCP] Enumerating and Abusing APIs
- 보안/OSCP
- 2024. 10. 29.
- Start up the Walkthrough VM 1 and modify the Kali /etc/hosts file to reflect the provided dynamically-allocated IP address that has been assigned to the offsecwp instance. Use Firefox to get familiar with the Developer Debugging Tools by navigating to the offsecwp site and replicate the steps shown in this Learning Unit. Explore the entire WordPress website and inspect its HTML source code in order to find the flag.
--> OS{f75a596a45aed1d6a0dbc86838727b00}
--> sudo vi /etc/hosts에 IP offsecwp를 추가하고 esc -> wq!로 저장하고 나온다
offsecwp로 접속하보면 접속이 잘된다. 그 후 접근해서 돌아다니다 "os{"로 검색해보면 플래그를 찾을 수 있다.

2.Start Walkthrough VM 2 and replicate the curl command we learned in this section in order to map and exploit the vulnerable APIs. Next, perform a brute force attack to discover another API that has a same pattern as /users/v1. Then, perform a query against the base path of the new API: what's the name of the item belonging to the admin user?
--> bookTitle22
# echo {GOBUSTER}/v1 > pattern;
# echo {GOBUSTER}/v2 >> pattern;
# gobuster dir -u http://192.168.217.16:5002 -w /usr/share/wordlists/dirb/big.txt -p pattern
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.217.16:5002
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Patterns: pattern (2 entries)
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/books/v1 (Status: 200) [Size: 235]
/console (Status: 200) [Size: 1985]
Progress: 28619 / 20470 (139.81%)^C
[!] Keyboard interrupt detected, terminating.
Progress: 28639 / 20470 (139.91%)
# curl -i 192.168.217.16:5002
HTTP/1.0 200 OK
Content-Type: application/json
Content-Length: 84
Server: Werkzeug/1.0.1 Python/3.7.13
Date: Mon, 28 Oct 2024 21:46:32 GMT
{ "message": "PWK Vulnerable API", "Help": "This is a vulnerable API application" }
# curl -i 192.168.217.16:5002/books/v1
HTTP/1.0 200 OK
Content-Type: application/json
Content-Length: 235
Server: Werkzeug/1.0.1 Python/3.7.13
Date: Mon, 28 Oct 2024 21:47:00 GMT
{
"Books": [
{
"book_title": "bookTitle16",
"user": "name1"
},
{
"book_title": "bookTitle97",
"user": "name2"
},
{
"book_title": "bookTitle22",
"user": "admin"
}
]
}위 처럼 url의 패턴을 등록하고 gobuster를 통해 url을 획득한다(books/v1)
curl -i 명령어를 사용해서 admin을 찾고 타이틀을 입력하면 끝
3. This website running on the Exercise VM 1 is dedicated to all things maps! Follow the maps to get the flag.
-->
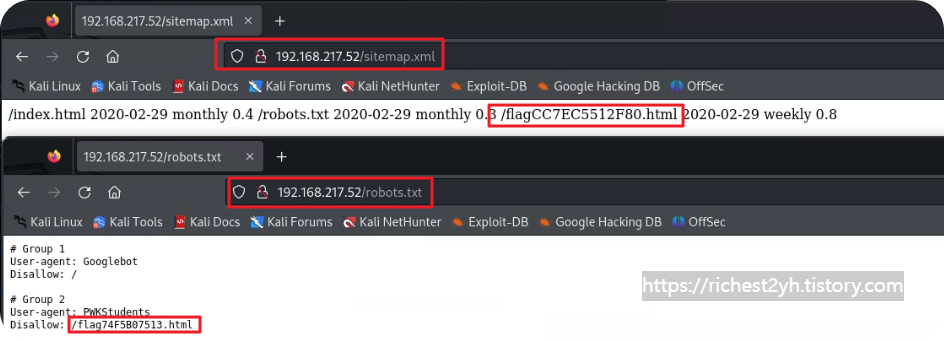
sitemap.xml과 robots.txt를 확인해보면 위와 같은 flag관련 url이 확인 되고 접근해보면 플래그가 쪼개져있다
합쳐서 넣으면 된다.

4. Inspect the Exercise VM 2 web application URL and notice if anything is interesting at the URL level.
--> OS{924448ee43db0551b0d9749a1bf617d1}
이번 연습문제는 어이없게 끝났다. 구경하려고 페이지 접근하니 바로 나오네 그런데 curl로 푸는 문제 같다

# curl -L 192.168.217.52
<meta http-equiv="refresh" content="0; URL=/?flag=%4f%53%7b%39%32%34%34%34%38%65%65%34%33%64%62%30%35%35%31%62%30%64%39%37%34%39%61%31%62%66%36%31%37%64%31%7d" />
curl을 사용할 때 서버에서 리다이렉션이 발생하면, -L 옵션을 사용하여 리다이렉션을 자동으로 따라가도록 설정
# echo "%4f%53%7b%39%32%34%34%34%38%65%65%34%33%64%62%30%35%35%31%62%30%64%39%37%34%39%61%31%62%66%36%31%37%64%31%7d" | xxd -r -p
OS{924448ee43db0551b0d9749a1bf617d1}
URL에서 인코딩된 flag 값을 디코딩하기 위해 다음 명령어를 사용
5. We made another website, but something is wrong. The site is available at Exercise VM 3, but it keeps giving some weird, non-standard responses. Check out the HTTP headers that accompany this site.
--> OS{56519367fd2721442d0577acfe07d56f}
힌트를 보니 http header에 특이사항이 있을것 같아 curl -i를 활용해서 헤더값 까지 확인 해보니
X-Something-Non-Standard 비표준적인 응답이 존재하며 ==로 끝나는것으로 보아 base64인코딩일것 같아서 디코딩 해보니 성공
# curl -i 192.168.217.52
HTTP/1.0 200 OK
Content-Type: text/html; charset=utf-8
Content-Length: 717
X-Something-Non-Standard: VGhlIGZsYWcgaXM6IE9TezU2NTE5MzY3ZmQyNzIxNDQyZDA1NzdhY2ZlMDdkNTZmfQ==
Server: Werkzeug/2.0.2 Python/3.9.9
Date: Mon, 28 Oct 2024 22:28:46 GMT
<!DOCTYPE html>
<html>
<head>
<title>Non-Standard Responses</title>
<style>
body {
width: 35em;
margin: 0 auto;
font-family: Tahoma, Verdana, Arial, sans-serif;
}
</style>
</head>
<body>
<h1>Welcome to Non-Standard Responses!</h1>
<p>Unfortunately, this website seems to be broken. It keeps giving out some <em>non-standard responses</em>.
I do not know that has gotten into its <em>head</em>. You should come back later once we have this under control.
Or, if you are really bored, you can investigate it more and let us know if you figure out what is going on.</p>
<p>This site reminds me so much of the default nginx template for some reason. So strange....</p>
</body>
</html>
# echo "VGhlIGZsYWcgaXM6IE9TezU2NTE5MzY3ZmQyNzIxNDQyZDA1NzdhY2ZlMDdkNTZmfQ==" | base64 -d
The flag is: OS{56519367fd2721442d0577acfe07d56f}6. We made another website, but something is wrong. The site is available at Exercise VM 3, but it keeps giving some weird, non-standard responses. Check out the HTTP headers that accompany this site.
--> OS{9d7006ae43f0c1a5443d20ffdf9c6e64}
힌트 내용과 같이 html, css, js 순서로 찾아보면 플래그가 숨어있다. 3개의 플래그를 합쳐주면 된다.
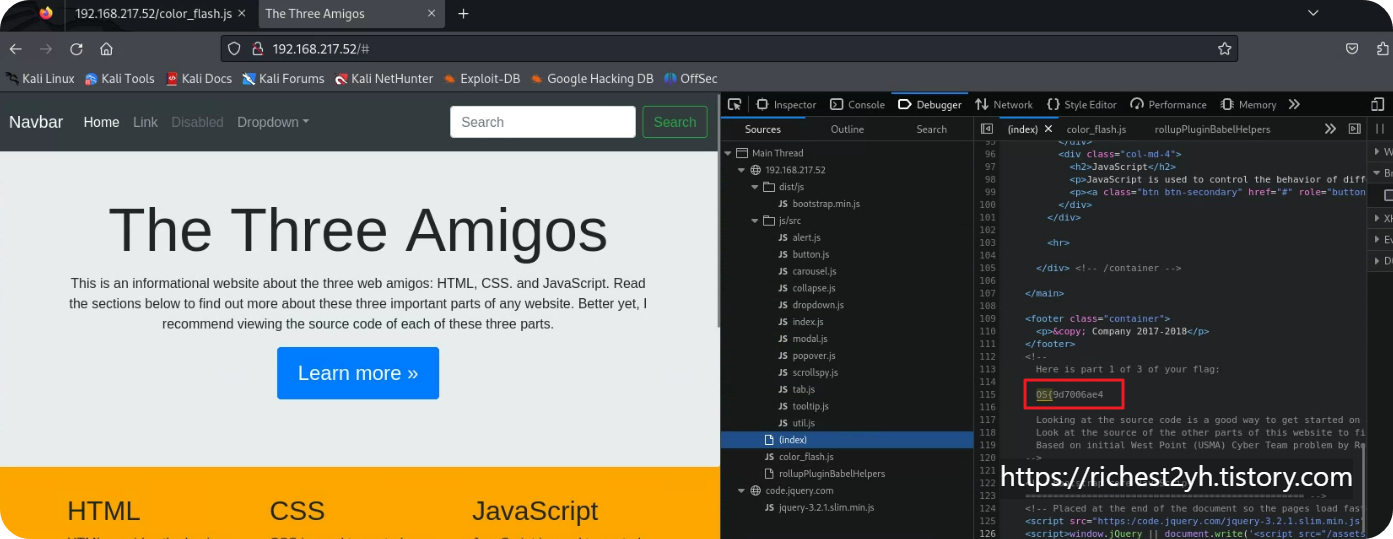
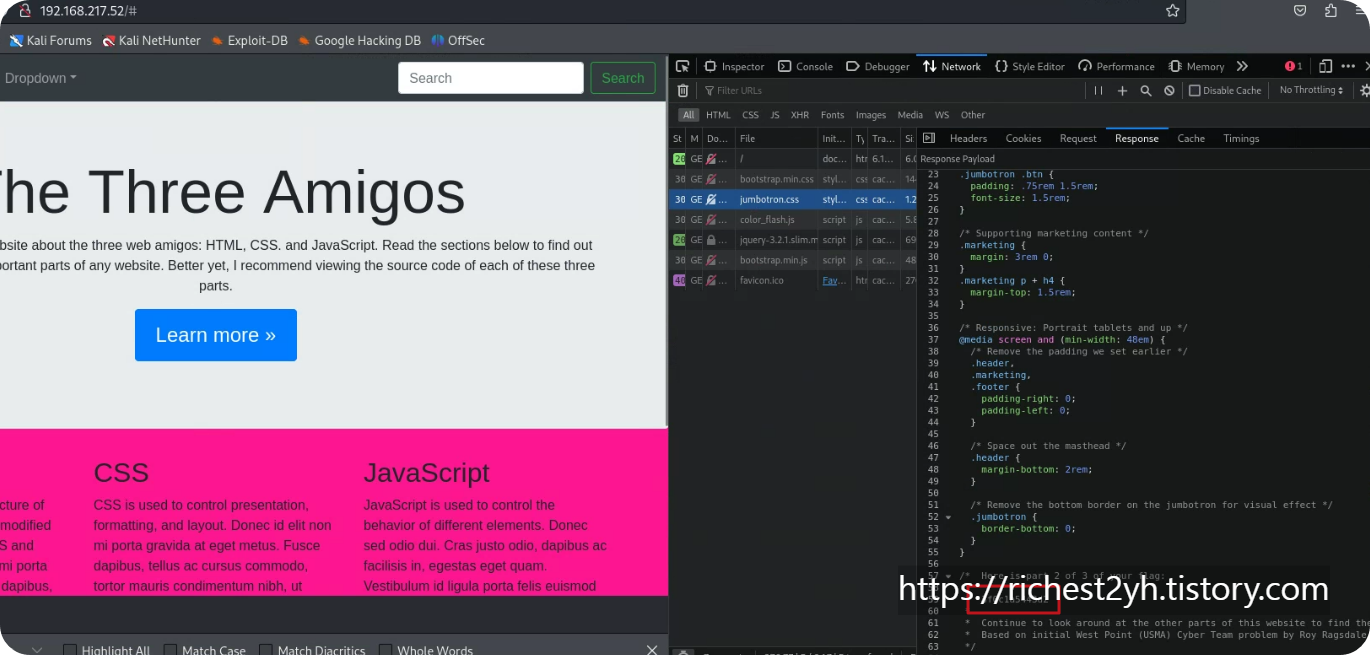
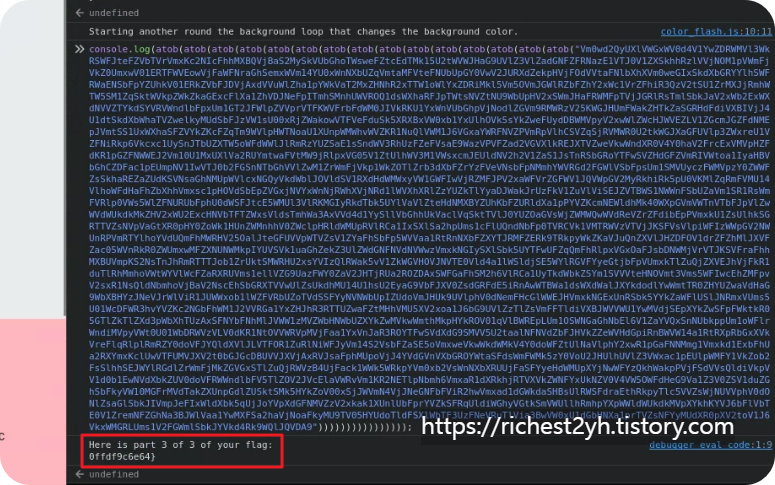
'보안 > OSCP' 카테고리의 다른 글
| [OSCP] XSS (Cross site script) (0) | 2024.11.01 |
|---|---|
| [OSCP] Cross-site script (0) | 2024.10.31 |
| [OSCP] Directory Brute Force with Gobuster (0) | 2024.10.28 |
| [OSCP] Nmap nse-vulnerability-scripts (2) | 2024.10.24 |
| [OSCP] Information Gathering - SNMP enumeration (0) | 2024.10.24 |