반응형
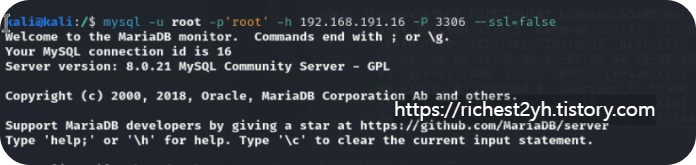
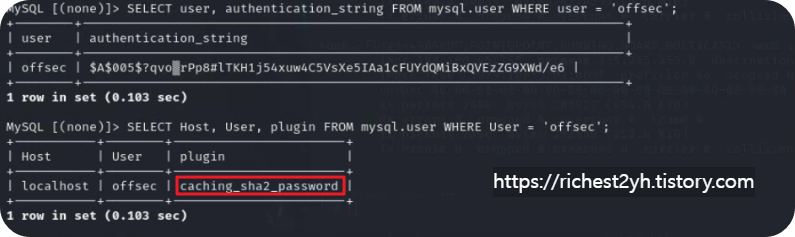
- From your Kali Linux VM, connect to the remote MySQL instance on VM 1 and replicate the steps to enumerate the MySQL database. Then explore all values assigned to the user offsec. Which plugin value is used as a password authentication scheme?
- --> caching_sha2_password
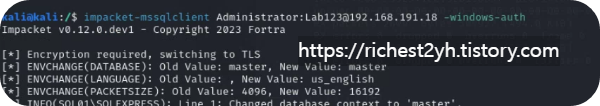
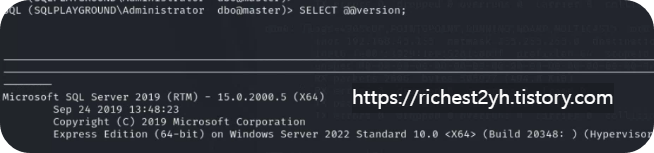
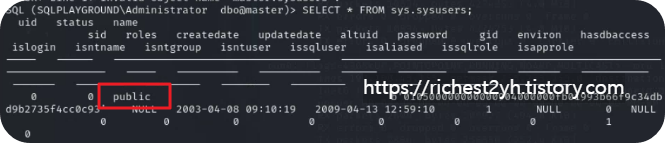
- From your Kali Linux VM, connect to the remote MSSQL instance on VM 2 and replicate the steps to enumerate the MSSQL database. Then explore the records of the sysusers table inside the master database. What is the value of the first user listed?
- -->public
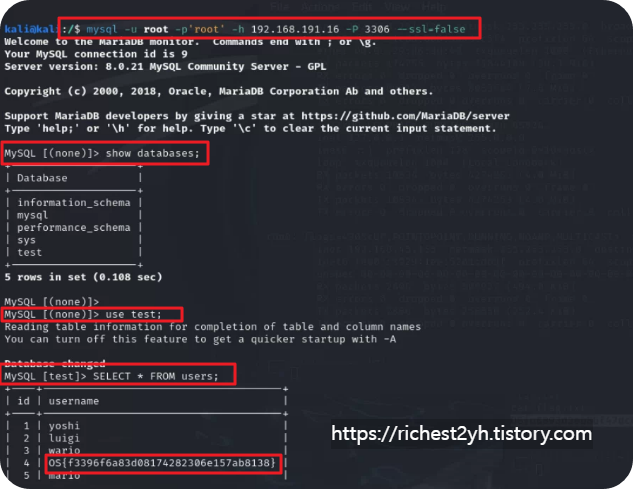
- From your Kali Linux VM, connect to the remote MySQL instance on VM 3 and explore the users table present in one of the databases to get the flag.
- --> OS{f3396f6a83d08174282306e157ab8138}
반응형
'보안 > OSCP' 카테고리의 다른 글
| [OSCP] Client-side Attacks - Information Gathering (0) | 2024.11.26 |
|---|---|
| [OSCP]Manual and Automated Code Execution SQL Injection attack (7) | 2024.11.25 |
| [OSCP]SQL Injection Attacks - SQL Theory and Databases (mssql) (0) | 2024.11.22 |
| [OSCP]SQL Injection Attacks - SQL Theory and Databases (mysql) (0) | 2024.11.21 |
| [OSCP]OS Command Injection (0) | 2024.11.18 |