반응형
- In this section, we used URL encoding to exploit the directory traversal vulnerability in Apache 2.4.49 on VM #1. Use Burp or curl to display the contents of the /opt/passwords file via directory traversal in the vulnerable Apache web server. Remember to use URL encoding for the directory traversal attack. Find the flag in the output of the file.
--> OS{9ca180636c5b6843678c569fde624361}
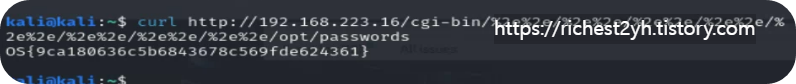
단순히 인코딩만 요하는 문제같다. 인코딩해서 curl 날려주면 된다.
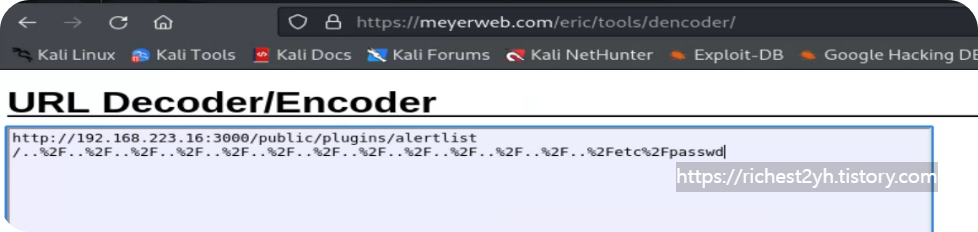
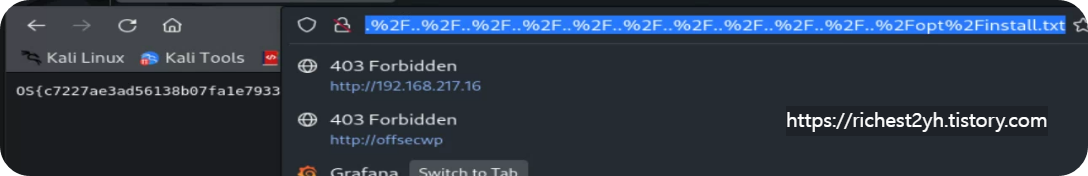
- Grafana is running on port 3000 on VM #2. The version running is vulnerable to the same directory traversal vulnerability as in the previous section. While URL encoding is not needed to perform a successful directory traversal attack, experiment with URL encoding different characters of your request to display the contents of /etc/passwd. Once you have a working request utilizing URL encoding, obtain the flag by displaying the contents of /opt/install.txt.
-->OS{c7227ae3ad56138b07fa1e793316e819}
먼저 /etc/passwd를 내용을 표시 하기 위해 다른 인코딩을 테스트 해보자
/ -> %2f를 통해 치환해서 etc/passwd를 찾으면 확인이 되고 문제의 답인 /opt/install.txt를 찾아보면 플래그를 찾을 수 있다.
반응형
'보안 > OSCP' 카테고리의 다른 글
| [OSCP] PHP Wrappers (0) | 2024.11.11 |
|---|---|
| [OSCP] Local file include (1) | 2024.11.08 |
| [OSCP] Directory Traversal (0) | 2024.11.06 |
| [OSCP] XSS (Cross site script) (1) | 2024.11.01 |
| [OSCP] Cross-site script (0) | 2024.10.31 |